Software is a pervasive element in most industrial products and processes nowadays. It comes from internal developments, from suppliers of sub-systems and chips, from outsourced development contractors, from open source repositories or simply from the previous work of the developers themselves. Software, unlike hardware, is easily replicable, accessible, copied and re-used. While large corporations could implement in-house procedures for software governance and compliance to legal obligations, small and mid-size businesses could not afford first generation tools for managed adoption of open source software and had to rely on training and trusting their developers, with some formal audits only when faced with a major sale, a merger & acquisition (MA) or other legally binding events.
Recently available second generation software lifecycle IP management tools enable open source adoption with a no training approach and without disturbance to established development processes.
Compliance to Legal Obligations
Open source software has become a significant player in most software development thanks to the wealth of source code available, its apparently free cost and its high degree of stability and security. Open source code is generally cost free. But it is not without obligations, as it comes laden with licensing and copyright conditions which are enforceable by law – sometimes with dire effects for the hapless users who are not careful to validate the pedigree of the code in their products; i.e. the provenance and the associated obligations of all software components.
This does not mean that outsourcing or the use of open source software is to be avoided. The issue is not with the use of open source, but with the unmanaged adoption without proper care to the copyright and licensing obligations it entails. It is paramount for industrial managers to validate the IP cleanliness of their products and services and ascertain that they meet all legal obligations before they reach the market.
Like most hardware products, software products need to have an associated Bill of Materials (BoM) that fully records the components in the product, their provenance and the licensing and copyright obligations each of them entail, making sure that there are no incompatibilities or violations. An adequate software BoM is instrumental in determining the legal compliance of the software and provides the necessary assurance to customers. As such, it can minimize the cost of indemnification and other associated legal obligations.
Traditionally, IP cleanliness was done manually through rather expensive expert analyses and due diligence processes, mostly undertaken in advance of important financial transactions – a merger, an acquisition or a major commercial undertaking. Manual analyses are prone to error, consume expert resources, take a long time and are becoming prohibitively expensive nowadays, when software is so pervasive and the use of open source and outsourcing so prevalent.
Fortunately, nowadays there are tools at our disposal to do such pedigree analyses automatically - on demand, on schedule or even in real-time within the development process. Some of these tools allow the analyses to be done in accordance with corporate IP policies and lend themselves well to an institutionalization of proper record keeping and safe software development practices.
As the critical factors driving the economics of software management are the efforts to fix the software IP issues and the associated delays in product introduction to market, everything should be done to catch IP issues as soon as possible in the development process rather than wait until the product is finished.
Critical Elements of Software IP Management
The critical elements of software IP management in an organization are:
- The existence of an IP policy for each project undertaken and a process to disseminate and apply it. This includes the adequate education of personnel involved. Corporate IP policies must be based on the organizations’ business goals and they should be clear and enforceable. They need to show the acceptable licenses, the approved vendors, what is restricted, and what should be done if unknown or unacceptable code is being brought into the organization’s software.
- The availability of a central code library, which includes the legacy code in the organization, together with an automated process for ascertaining the pedigree of all components to ensure compliance to all legal obligations.
- The processes and tools for ascertaining the legal obligations and managing the IP of software created and/or acquired in the organization.
- The customer assurance and support concerning the quality and IP cleanliness of software provided.
The best results are obtained when record keeping and IP management are treated as integral parts of the software development and quality assurance process:
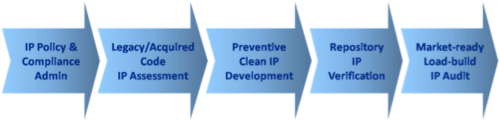
- The establishment and enforcement of an organization software IP policy commensurate with the corporate business goals. Large organizations may choose to establish IP policies appropriate for each class of project (software) they are undertaking.
- The creation of a central (legacy) code library for the enterprise (organization) and its subsequent analysis for the establishment of an associated pedigree database, which should capture the provenance and legal obligations associated with each code component in the enterprise (organization) code portfolio.
- The intellectual property audit and interpretation of the existing software status with adequate follow-up actions to remedy any policy violations.
- The enforcement of IP cleanliness assurance for any software acquired from outsourced development partners.
- The real-time gathering of software records for all new source code created or brought into the organization by its developers.
- Preventive analysis of each new software component to ensure that it meets the corporate IP policy.
- Alerting developers if code brought into the project does not meet corporate IP policy, together with instructions on what to do in order to alleviate the situation in real-time.
- The completion of a software BoM which contains information on all components, including their origin, licensing obligations, supplier history, version, and all other pertinent information for proper life-time management.
Automatic Tools for Efficient Adoption of Open Source
Second generation automatic tools for record keeping and source code portfolio management have been made available recently to help companies lower development and legal costs, reduce time-to-market and lower business risks.
Using such tools makes it possible to implement a simple and efficient process for managed open source software adoption which would allow developers the freedom of selecting best solutions appropriate with the corporate policy. The main stages of such a process are:
- Central definition of an Intellectual Property (IP) and legal compliance policy acceptable to the organization project.
- This stage is initiated by development/business manager together with legal counsel and captured by the appropriate tool for software IP analysis.
- This stage also captures the mandated workflow in case of detection of policy violations in the course of subsequent code analyses and software development activities.
- More advanced tools enable the definition of several IP policies to suit specific projects.
- Legal compliance analysis of legacy code or of code acquired from suppliers or subcontractors.
- A software IP analyzer is used at this stage to map the software content and determine the pedigree of each software component – be it open source, internal proprietary or commercial. Usually, the analysis is done by comparing code characteristics (signatures) with huge databases that contain the signatures of publicly available and some proprietary software libraries.
- A pedigree database of analyzed code is established for further reference.
- A report detailing the composition of the analyzed code, the matching external content and the associated legal obligations is made available to authorized personnel.
- On notification of a file being checked-in, an automatic IP analysis is performed and the file’s IP attributes are checked against established IP policies.
- The pedigree database is automatically updated when a source file is saved or checked-in to the code repository.
- If any violations are detected, an alert is provided, as specified by the mandated workflow in the IP policy.
- Advanced software IP management tools can operate unobtrusively at each developer workstation to detect any new code being brought into a project, determine its pedigree and verify that it meets requirements of IP policy associated with that project.
- No developer training is necessary.
- The pedigree database is automatically updated when a source file is saved or checked-in to the code repository.
- Developers are notified only if there is a violation of the IP policy, in which case they are requested to justify acceptance of code (e.g. for internal use only) or to change it for acceptance by IP policy.
- Development managers can also be alerted as specified by the mandated workflow in the IP policy.
- An interactive report detailing the content and legal obligations of the analyzed code is available on demand by authorized personnel.
- The software build load is automatically analyzed and its pedigree is checked against specified IP policy.
- The associated pedigree database is updated.
- Any violations of IP policy is notified for appropriate action.
- A software BoMs is provided together with information on compliance to legal obligations as per established IP policy.
This software lifecycle management process ensures automatic compliance with appropriate IP policies without imposing specific pre-approval of open source components. An optional stage dedicated to pre-approval of open source components and the management of a repository of approved open source can be considered as part of stage 3 above.
Done properly, software IP management should be unobtrusive to the developers, requiring their attention only when code of unknown or unacceptable pedigree is brought into the software.
Second generation tools for software lifecycle management have been designed from the beginning for easy adoption and application, do not require any special training of developers, are affordable even for small companies and provide automatically a software BoM which can attest the compliance to legal obligations.
Mahshad Koohgoli is the CEO of Protecode, Inc., based in Ottawa, Ontario, Canada. He has more than 25 years of experience in the telecommunications industry and specializes in technology start-up businesses. Mahshad has a BSc and a PhD from the University of Sussex, England. Sorin Cohn-Sfetcu has 30 years of international business and technology experience. He holds several patents in Web services, wireless, and digital signal processing.
Mahshad: 613-721-5936
[email protected]
Sorin: 613-301-0066
[email protected]

